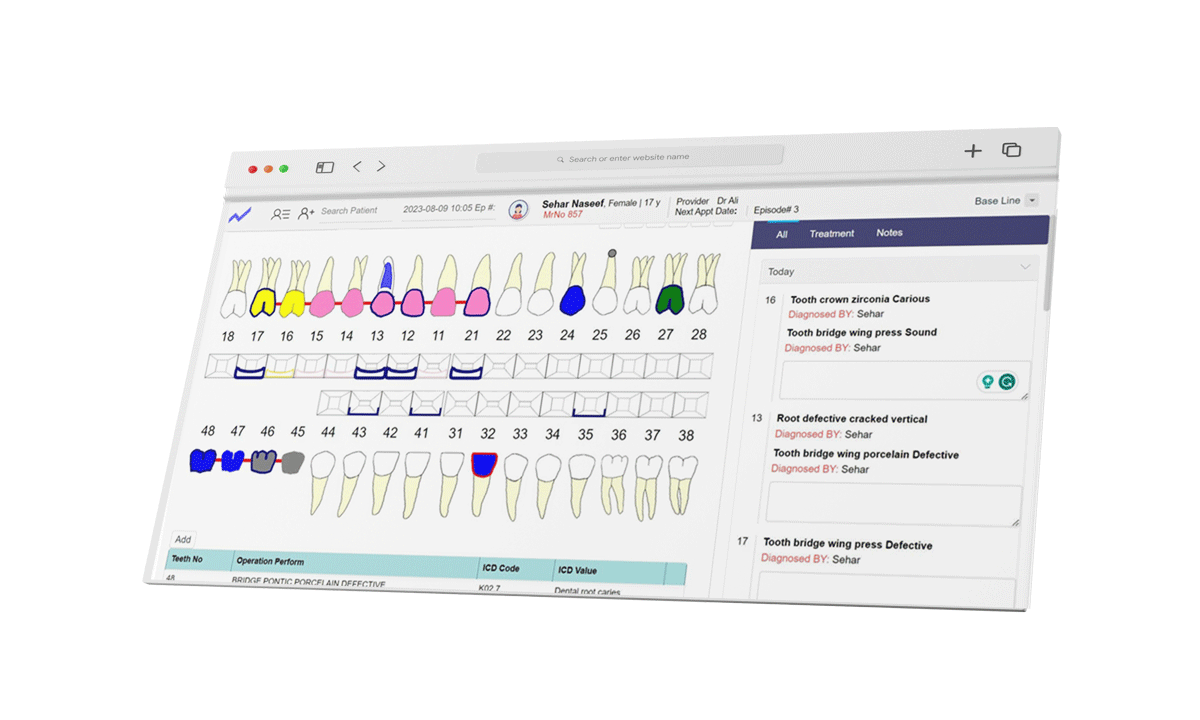
Cloudpital # 1 is one of the top EMR systems world that is healthcare Electronic Medical Records have revolutionized the way patients receive care by facilitating efficient management of data and improved communication between healthcare professionals. But, with the ease of electronic records comes the obligation of protecting sensitive information about patients. Secure security measures are essential to safeguard patient data in EMR systems, assuring security, confidentiality, and accessibility. This is a complete description of security measures that have been implemented to secure EMR systems from potential dangers.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Cloudpital # 1 EMR systems
What security measures to protect patient data within EMR systems?
Access Control
-
The Role Based Access feature
EMR systems uses role-based control of access, which grants different levels of access for users according to their responsibilities and roles within the healthcare institution. This restricts access for anyone who is not authorized to sensitive information.
-
Strong Authentication
Multiple-factor security (MFA) is typically mandated, which requires users to present various forms of proof like biometrics, passwords or smart cards in order for accessing the system, thereby increasing security.
-
Session Management
The strictest sessions management protocols ensure that sessions of users are secure started, maintained, and closed, which reduces the chance of unauthorized access through session hijacking or fixation.
Data Encryption
- The encryption of patient information stored in EMR databases is encrypted with advanced cryptographic techniques, rendering the data unreadable and inaccessible for unauthorized users, even if the storage media is damaged.
- Transmitting data encrypted Data that is transmitted between various elements of an EMR systems, like clients and servers, is encrypted with encryption protocols that are secure, such as TLS (Transport Layer Security) which prevents eavesdropping as well as interception during the course of transport.

What security measures to protect patient data within EMR systems?
Audit Trails and Logging
- Complete Logging EMR system keep detailed audit trail and logs of all user activity that include modification attempts and access and views of data. These logs are essential evidence to assist in looking into security breaches and incidents.
- Continuous Monitoring: Computerized systems continually check the charting for suspicious activity or anomalies, and trigger alerts to investigate immediately and prompt intervention by security personnel.
Physical Security Measures
- Data Center Security Access to data centers that house EMR servers is monitored through measures like biometric security, authentication, surveillance cameras as well as security staff, which reduces the possibility of physical access.
- Secure Devices: The mobile devices that are used for accessing EMR systems, like smartphones or tablets are protected by devices-level encryption remote wipe capabilities and strong authentication mechanisms that ensure that data is not exposed in the event of theft or loss.
Data Integrity Controls
-
Digital Signatures
Digital signatures can be used to verify the authenticity and authenticity of medical records that are stored in electronic format to ensure that the information is not altered or altered in the process of storage or transmission.
-
Data Validation
EHR use methods of validation to ensure the accuracy and reliability of patient data, and prevent the entry of incorrect or hacked information that could harm patient security or privacy.
Disaster Recovery and Redundancy
-
Backup and Recovery
Continual back-ups for EMR data are made and stored in various geographical locations, which allows for quick recovery in the event the loss of information or system failure caused by cyber-attacks or natural disasters or other unexpected events.
-
High availability
Reliable infrastructure and failover systems are employed to ensure continuous accessibility to EMR systems which reduces downtime and ensures continuity of patient care in the event of an emergency.
Regulatory Compliance
-
HIPAA Conformity
EMR systems adhere to the Health Insurance Portability and Accountability Act (HIPAA) regulations that establish stringent guidelines for ensuring the confidentiality and security of patients’ health information stored in electronic format.
-
Information Breach Notification
In accordance with the regulatory requirements healthcare providers promptly inform patients and other authorities of a breach in data security or disclosure that is not authorized of patient information, which facilitates prompt remediation and mitigation efforts.
User Training and Awareness
-
Security Awareness Training
Health care professionals and their staff are regularly trained in sessions and awareness programs about the best practices to protect patient information, which includes security of passwords along with phishing awareness and procedures for handling data.
- In the event of an incident, healthcare facilities organize drills and training to train staff on how to respond effectively to security incidents, and ensuring quick resolution and rapid containment. minimize the impact on patients’ security and privacy.
Conclusion
In the end, protecting the patient’s data in EMR systems is essential for ensuring trust and security when it comes to healthcare delivery. Implementing a multi-layered strategy including access control and encryption, auditing physically secure, integrity checks such as disaster recovery, regulations compliance as well as user education healthcare institutions can minimize the risks and protect their EMR systems to protect against ever-changing cyber-attacks. Constant vigilance and proactive risk management and compliance with industry best practices are vital to safeguard the privacy of patient data in the age of digital.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
EMR systems
EMR systems
EMR systems
What security measures to protect patient data within EMR systems? similar software solutions prices were updated on 2024-04-29T20:03:46+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2024-04-29T20:03:46+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2024-04-29T20:03:46+00:00 Price is SAR 100 and this was updated on updated on 2024-04-29T20:03:46+00:00 similar What security measures to protect patient data within EMR systems? software solutions prices were updated on 2024-04-29T20:03:46+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2024-04-29T20:03:46+00:00 Price is SAR 100 and this was updated on updated on 2024-04-29T20:03:46+00:00
29-1-2024