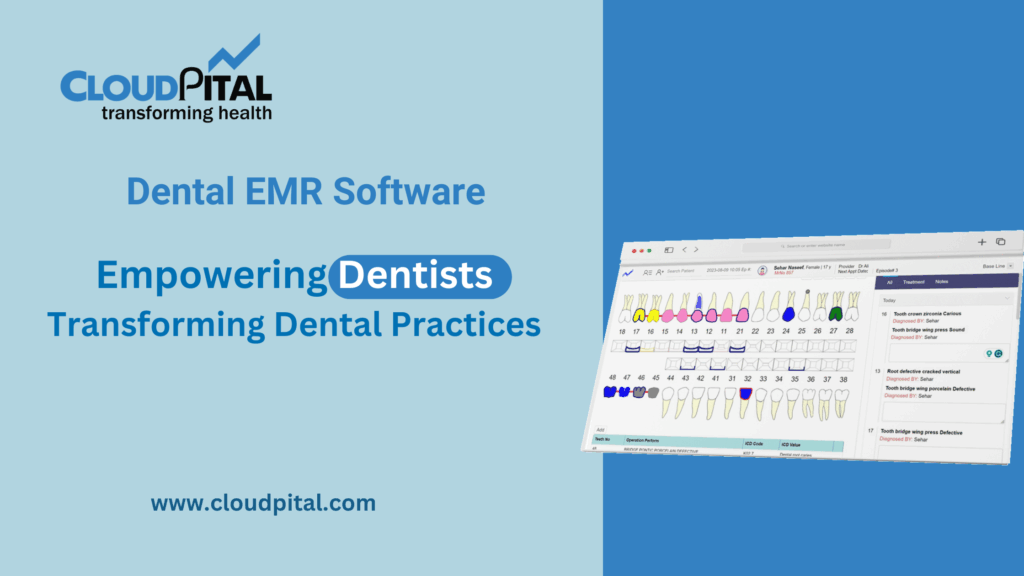
Cloudpital # 1 one of the top Medical Solutions has been a growing concern in this new age where health care is highly technological. EHR, telemedicine, mobile health apps, and IoT devices have made healthcare delivery very efficient but also subjected sensitive patient information to cyber risks. It is therefore crucial to offer patient data security medical solutions to protect privacy and sure systems in health care. This blog is going to discuss the various means by which current medical solutions increase the security of patient information and make digital transformation easier for healthcare providers.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@bilytica.com
Cloudpital # 1 Medical Solutions

Encryption of Patient Data
One of the most basic ways that patient information is protected is through encryption. Encryption takes data and transforms it into coded data, so that it cannot be read unless a decryption key is provided. Strong Medical Solutions use robust encryption programs to ensure that data like patient health records, diagnoses, and billing information are safe as it is saved in databases or transmitted across networks.
Both at-rest and in-transit encryption are important
- At-rest encryption protects information stored on servers, cloud systems, and devices.
- In-transit encryption guards data when transferred between devices, such as telemedicine consultations or any form of data transfer from one hospital to another.
- AES-256, end-to-end encryption (E2EE), and even transport layer security in the form of online transmission are some common ways health care providers protect against unauthorized access into their patients’ data.
Access control mechanisms
Another significant factor in data security is the management of who should access the patient’s information. The medical solutions enhance patient data security through role-based access control, known as RBAC, and multi-factor authentication, that only those staff authorized have a chance to access the sensitive data.
Role-Based Access Control (RBAC): This access control is job-oriented, where clinicians, nurses, administrative staff, and technicians can only access that information necessary to the job at hand. A nurse might have access to patient medical information but not to billing information.
Multi-Factor Authentication: This helps to ensure that an individual has to be verified through multiple ways apart from just a password, be it, for instance, fingerprint scanning or just one-time code.
The above technologies help minimize fraudulent access to your patient data both from internal and external threats.
Data Anonymization and Masking
Data anonymization and masking are methods that are applied to prevent identification of patient information. In most instances, healthcare providers and researchers seek access to data for conducting analyses and studies. Sometimes these parties, however, may not require PII.
- Data Anonymization removes PII including a patient’s name, the Social Security number, and any data that, through aggregation, can be traced back to an identifiable patient.
- Data Masking hides sensitive details of data, which may be shown as any other method, like showing only the last four digits of a patient’s ID or by partial masking sensitive information.
- These techniques allow health organizations to use and share data without violating confidentiality in patients; thus, it is an essential method in large-scale health research and sharing projects.
Blockchain for Secure Data Management
Blockchain technology is increasingly being embraced in Medical Solutions for the reason that it creates records that are secure, transparent and not amendable. Blockchain works as a decentralized ledger wherein every transaction is confirmed by a network of computers stored in “blocks” which are chronologically linked.
Blockchain can be applied to healthcare to:
- Store Patient Records in a Tamper-Proof Manner with tamper-proof data entries.
- Allow interoperability between providers by granting access to data in a safe and efficient manner.
- Ensure it has full audit trail so that whoever accessed the data will have an audit trail associated with it, thus eliminating unauthorized access.
- Blockchain is decentralized, thus not permitting any alteration of data within the chain. Such a technology, therefore, is promising for use in securing sensitive patient data.

Artificial Intelligence for Threat Detection
AI proves to be invaluable in identifying and mitigating cyber threats in real time. PMS powered by AI can ensure that the patient data is kept safe and sound by observing network activities, tracing unusual behavior, and reacting to potential threats before they shift to a more dangerous trend.
AI algorithms can help in
- Anomaly detection, which involves anything from unusual login attempts to unusual data access patterns.
- Identification of malware and ransomware before it intrudes systems.
- Automate any response to suspected breaches, for example, locking access in case of detected suspicious activity.
- This proactive approach to threats by AI-powered solutions in the medical industry helps minimize the risks of data breaches and patient information exposure.
Data Backup and Disaster Recovery Solution
It provides data backup and disaster recovery solutions so that patient data is not lost due to cyberattacks, system failures, or natural disasters. Automated data backup procedures in medicine solutions with disaster recovery plans allow health care organizations to recover patient information quickly in a secure environment.
- Automated Data Backups ensure there are copies of patient data regularly stored in a secure environment at different locations.
- Disaster Recovery Plans outline how data may be recovered and operations kept moving in the wake of a system breach.
- Solutions from this category make health care providers not only enable data recovery but also minimize downtime and prevent potential losses in data, which will cause patients to experience delay in care processes.
Compliant Data Protection Solution
Regulatory compliance is among the key requirements of health care data security. Data protection law-based medical solutions ensure that health care organizations maintain regulatory standards and patient privacy. Some of these regulations include:
- HIPAA in the United States
- GDPR for health care organizations operating under the European Union
- CBAHI in Saudi Arabia.
- Such rules set strict standards for the way patient information must be managed, including access controls, retention policies, breach notification obligations, and others. Compliant medical solutions are an effective way to ensure that all of these regulations are followed by healthcare providers, hence protecting their integrity in addition to protecting patient information.
Telemedicine Security Protocols
Telemedicine has become the order of the day in modern health care, but simultaneously, it raises specific data security issues. Telemedicine solutions have incorporated various security measures that safeguard patient data during virtual meetings with healthcare providers.
Some of them include the following:
Video Conferencing: Security through Encryption: The video conferencing tools need to be encrypted and support privacy standards such as HIPAA to ensure all the interactions between a patient and the provider are private.
Authentication of Patient and Provider: Most telemedicine interfaces, before accessing the system, will demand identity verification from patients and providers thus providing no scope for improper access.
Data Encryption: Any data exchanged in a telemedicine session, medical images to results of lab tests, must be encrypted to make sure the private information of patients is not leaked.
Telemedicine, therefore, with these security measures, provides assured high-quality care to patients without compromising their data privacy.
IoT Device Security Measures
IoT devices include wearable health monitors and smart medical devices. The enormous amounts of data that such devices collect make the patients vulnerable to this threat. While these devices help improve healthcare providers’ insights into the health of their patients, vulnerabilities in the system pose cyberattacks to many of these devices. Securing IoT devices is therefore important to ensure no one illegally gains entry to the patient’s data.
The following are some of the common practices on security:
Regular Firmware Updates: This is the way through which one ensures that his IoT devices are updated with the latest security patches and thus prevents them from being wrongly exploited in any point of their vulnerability.
Authentication of the device: Thus, access is limited only to authorized devices such that unauthorized devices may not gain access to sensitive patient data.
Secure Data Transference: The data collected by IoT devices should be transmitted to healthcare systems in encrypted form, thus avoiding interception.
IoT devices thus secure wearable technology for healthcare providers and place them at liberty to use wearable technology in monitoring patient health and gathering real-time information without exposing patient data to unnecessary risks.
Education of Healthcare Professionals and Patients to Data Security
This ultimately comes down to the fact that technology alone cannot secure patient date. Human error actually remains a major risk to date security to this date. RCM that ensure user education and training for healthcare professionals and patients help them understand the importance of date security and their ways of self-protection.
Conclusion
This is the case with anti-phishing along with other social engineering attack detection for preventing unauthorized access; password management as well as device security advice on how to reduce risks of theft of credentials; health solutions are, therefore, used responsibly and safely by training staff and patients to make informed decisions that preserve data security.
With healthcare continuing to go digital, it has become more than important to protect patient information. Encryption of data, access control, AI-based threat detection, and regulatory compliance in medical solutions allow health care service providers to hold sensitive information securely while improving the efficiency of work procedures. Telemedicine, IoT devices, as well as cloud-based health systems make security measures no longer optional but a basic requirement for protecting patient privacy.
Investments in secure medical solutions, including ensuring protection of data, form the base that provides health care providers with a sense of trust from their patients, success in regulations and quality care delivery in a secure environment. Indeed, amidst the evolving and seemingly endless cyber threats around the world, securing patient data is crucial for the success of modern health care systems.
You can explore our other blogs
Medical Solutions, EMR Systems, RCM
How do Medical Solutions enhance patient data security? similar software solutions prices were updated on 2025-07-01T22:56:38+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2025-07-01T22:56:38+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2025-07-01T22:56:38+00:00 Price is SAR 100 and this was updated on updated on 2025-07-01T22:56:38+00:00 similar How do Medical Solutions enhance patient data security? software solutions prices were updated on 2025-07-01T22:56:38+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2025-07-01T22:56:38+00:00 Price is SAR 100 and this was updated on updated on 2025-07-01T22:56:38+00:00
11-12-2024