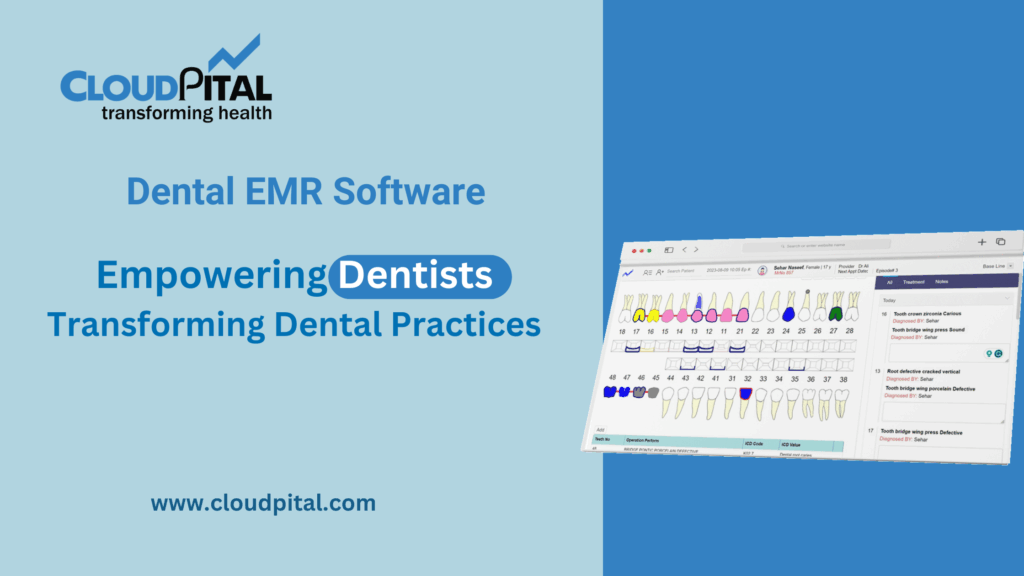
Cloudpital # 1 is one of the top Remote Patient Monitoring are of paramount importance, particularly when it comes to Remote Patient Monitoring (RPM) systems. These systems collect, transmit, and store sensitive patient data, making them a potential target for cyber threats. Ensuring robust data privacy and security is crucial to maintaining patient trust, complying with regulations, and protecting against data breaches. Below is a comprehensive overview of the measures and strategies employed to safeguard data within RPM systems.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@cloudpital.com
Cloudpital # 1 Remote Patient Monitoring

Encryption
Encryption is the cornerstone of data security in Remote Patient Monitoring systems. It ensures that data is unreadable to unauthorized users during transmission and storage. There are two primary types of encryption used:
- Transport Layer Security (TLS): This protocol secures data during transmission between the patient’s device and the RPM system. TLS encrypts the data packets, making it difficult for hackers to intercept and decipher the information.
- Advanced Encryption Standard (AES): This is used for encrypting data at rest within the RPM system. AES-256, a robust version of AES, is commonly employed to protect stored data from unauthorized access.
By implementing these encryption standards, RPM systems ensure that patient data remains confidential and secure both in transit and at rest.
Authentication and Authorization
Authentication and authorization mechanisms are critical for controlling access to the RPM system and its data. These processes verify the identity of users and ensure they have the appropriate permissions to access certain data or perform specific actions. Key methods include:
- Multi-Factor Authentication (MFA): MFA requires users to provide two or more verification factors to gain access. This could include something they know (password), something they have (smartphone), and something they are (fingerprint or facial recognition). MFA significantly reduces the risk of unauthorized access.
- Role-Based Access Control (RBAC): RBAC restricts system access based on the user’s role within the organization. For example, a nurse might have access to different data and functionalities compared to a physician. This ensures that users can only access the information necessary for their job functions.
- Single Sign-On (SSO): SSO allows users to log in once and gain access to multiple related but independent systems without having to log in again. This simplifies user access while maintaining security controls.
Compliance with Regulations
Compliance with healthcare regulations is essential for ensuring data privacy and security. Remote Patient Monitoring systems must adhere to several key regulations:
- Health Insurance Portability and Accountability Act (HIPAA): In the United States, HIPAA sets the standard for protecting sensitive patient data. RPM systems must implement administrative, physical, and technical safeguards to ensure HIPAA compliance. This includes encryption, access controls, audit controls, and regular risk assessments.
- General Data Protection Regulation (GDPR): For systems used in the European Union, GDPR compliance is mandatory. GDPR requires stringent data protection measures, including obtaining explicit consent from patients, ensuring data minimization, and providing patients with the right to access, correct, and delete their data.
- Health Information Technology for Economic and Clinical Health (HITECH) Act: This act promotes the adoption of health information technology and strengthens HIPAA by increasing penalties for breaches and requiring breach notifications.
Compliance with these regulations ensures that RPM systems not only protect patient data but also avoid legal penalties and maintain patient trust.

Regular Security Audits and Assessments
Conducting regular security audits and risk assessments is crucial for identifying and mitigating potential vulnerabilities in the Hospice nursing system. These practices include:
- Internal Audits: Regular internal audits help identify security gaps and ensure compliance with established policies and procedures. They involve reviewing access logs, testing encryption methods, and verifying the implementation of security controls.
- Third-Party Penetration Testing: Engaging external experts to conduct penetration testing can reveal vulnerabilities that internal teams might overlook. These tests simulate cyber-attacks to evaluate the system’s defenses and resilience.
- Vulnerability Scanning: Automated tools can continuously scan the RPM system for known vulnerabilities. This proactive approach allows for timely patching and mitigation of security risks.
Regular assessments and audits help maintain a high security standard and ensure that any emerging threats are addressed promptly.
Data Anonymization and De-Identification
To further protect patient privacy, RPM systems can employ data anonymization and de-identification techniques. These methods involve removing or encrypting personal identifiers from the data, making it difficult to trace back to the individual. Common techniques include:
- Data Masking: This process replaces sensitive data elements with fictional equivalents, allowing the use of data in development and testing environments without compromising privacy.
- Aggregation: Aggregating data from multiple patients into a single dataset can protect individual privacy while still providing useful information for analysis and research.
- Pseudonymization: This technique replaces personal identifiers with pseudonyms or codes, which can only be re-identified with additional information that is kept separately.
By implementing these techniques, RPM systems can use and share patient data for analysis and research without exposing individual identities.
Secure Data Storage Solutions
The storage of patient data must be secure to protect against unauthorized access and breaches. This includes:
- Cloud Security: For RPM systems utilizing cloud storage, it is crucial to choose cloud service providers that comply with industry standards and regulations. Providers should offer robust security features such as data encryption, access controls, and regular security audits.
- On-Premises Storage: For organizations that prefer to store data on-site, implementing physical security measures (such as restricted access to data centers) and technical controls (such as firewalls and intrusion detection systems) is essential.
- Backup and Disaster Recovery: Regular backups and a comprehensive disaster recovery plan ensure data availability and integrity in case of system failures or cyber-attacks. Encrypted backups stored in multiple locations protect against data loss and unauthorized access.
Secure storage solutions are fundamental to maintaining the confidentiality, integrity, and availability of patient data within RPM systems.
User Education and Training
Educating users about security best practices is vital for minimizing human error, which is often the weakest link in data security. Training programs should include:
- Phishing Awareness: Educating users about phishing attacks and how to recognize suspicious emails and links can prevent Ophthalmology EMR in Saudi Arabia access and data breaches.
- Password Management: Encouraging the use of strong, unique passwords and secure password managers helps protect user accounts from being compromised.
- Data Handling Practices: Training on proper data handling procedures, such as not sharing sensitive information over unsecured channels, ensures that users follow best practices for data privacy and security.
Regular training and updates on emerging threats and security protocols help maintain a security-aware culture within the organization.
Incident Response Plan
Having a robust incident response plan in place is crucial for effectively handling data breaches and security incidents. The plan should include:
- Identification: Quickly identifying potential security incidents through monitoring and alert systems.
- Containment: Containing the breach to prevent further damage, which might involve isolating affected systems and blocking unauthorized access.
- Eradication: Removing the root cause of the breach, such as malware or compromised accounts, to prevent recurrence.
- Recovery: Restoring affected systems and data from backups and ensuring that systems are secure before resuming normal operations.
- Post-Incident Analysis: Conducting a thorough review of the incident to understand its cause, impact, and effectiveness of the response, and implementing measures to prevent future incidents.
An effective incident response plan minimizes the impact of security breaches and helps the organization recover swiftly while maintaining patient trust.
Conclusion
Ensuring data privacy and security in Remote Patient Monitoring systems is a multifaceted process that involves a combination of technical measures, regulatory compliance, regular audits, user education, and robust incident response strategies. By implementing strong encryption protocols, authentication mechanisms, compliance with regulations, and regular security assessments, RPM systems can protect sensitive patient data from unauthorized access and cyber threats. Data anonymization, secure storage solutions, and comprehensive user training further enhance the security framework. With these measures in place, RPM systems can provide reliable and secure healthcare monitoring, ultimately improving patient outcomes while safeguarding their privacy.
Click to Start Whatsapp Chatbot with Sales
Mobile: +966547315697
Email: sales@cloudpital.com
Remote Patient Monitoring
Remote Patient Monitoring
Remote Patient Monitoring
How does Remote Patient Monitoring system ensure data privacy? similar software solutions prices were updated on 2025-07-03T02:58:56+00:00 in Saudi Arabia in Mecca, Medina, Riyadh, Khamis Mushait, Yanbu, Jeddah, Dammam, Unaizah, Uqair, Ha’il, Ta if, Al Bahah, Dhahran, King Abdullah Economic City, Najran, Diriyah, Qatif, Khafji, Jubail, Abqaiq, List of Cities and Towns in Saudi Arabia, Ras Tanura, Turubah, Jazan Economic City, Knowledge Economic City, Medina, Khobar, Abha, Tabuk, Saudi Arabia, similar software solutions prices were updated on 2025-07-03T02:58:56+00:00 We also provide in Saudi Arabia services solutions company in Hafar Al-Batin, Udhailiyah, Al-Awamiyah, Hofuf, Hautat Sudair, Buraidah, Tayma, Duba, ‘uyayna, Saihat, Al-Kharj, Al-ula, Jizan, Rumailah, Ar Rass, Arar, Shaybah, Al Majma’ah, Rabigh, Dhurma, Haradh, List of Saudi Cities by Gdp Per Capita, Badr, Sudair Industrial City, Baljurashi, Shaqraa, Al-Khutt, Habala, Ad Dawadimi, Dawadmi, Layla, similar software solutions prices were updated on 2025-07-03T02:58:56+00:00 Price is SAR 100 and this was updated on updated on 2025-07-03T02:58:56+00:00 similar How does Remote Patient Monitoring system ensure data privacy? software solutions prices were updated on 2025-07-03T02:58:56+00:00 in Saudi Arabia in Haql, Afif, Al-Abwa, Farasan, Al-Jaroudiya, Thadig, Al-Thuqbah, Al Wajh, Almardmah, Al-Zilfi, Muzahmiyya, Prince Abdul Aziz Bin Mousaed Economic City, Tharmada’a, Skaka, Um Al-Sahek, Sharurah, Tanomah, Bisha, Dahaban, Al Qunfudhah, Qurayyat, Saudi Arabia, Ha’ir, as Sulayyil, Al Lith, Turaif, Al-Gway’iyyah, Samtah, Wadi Ad-Dawasir, Az Zaimah, Safwa City, Jalajil, Harmah, Mastoorah, Hotat Bani Tamim, Jabal Umm Al Ru’us, Rafha, Qaisumah, Al-Ghat, Hajrah, Al-Hareeq. Excerpt: Jeddah (also spelled Jiddah, Jidda, or Jedda; Arabic: Jidda) is a Saudi Arabian city located on the coast of the Red Sea and is the major urban center of western Saudi Arabia similar software solutions prices were updated on 2025-07-03T02:58:56+00:00 Price is SAR 100 and this was updated on updated on 2025-07-03T02:58:56+00:00
17-5-2024